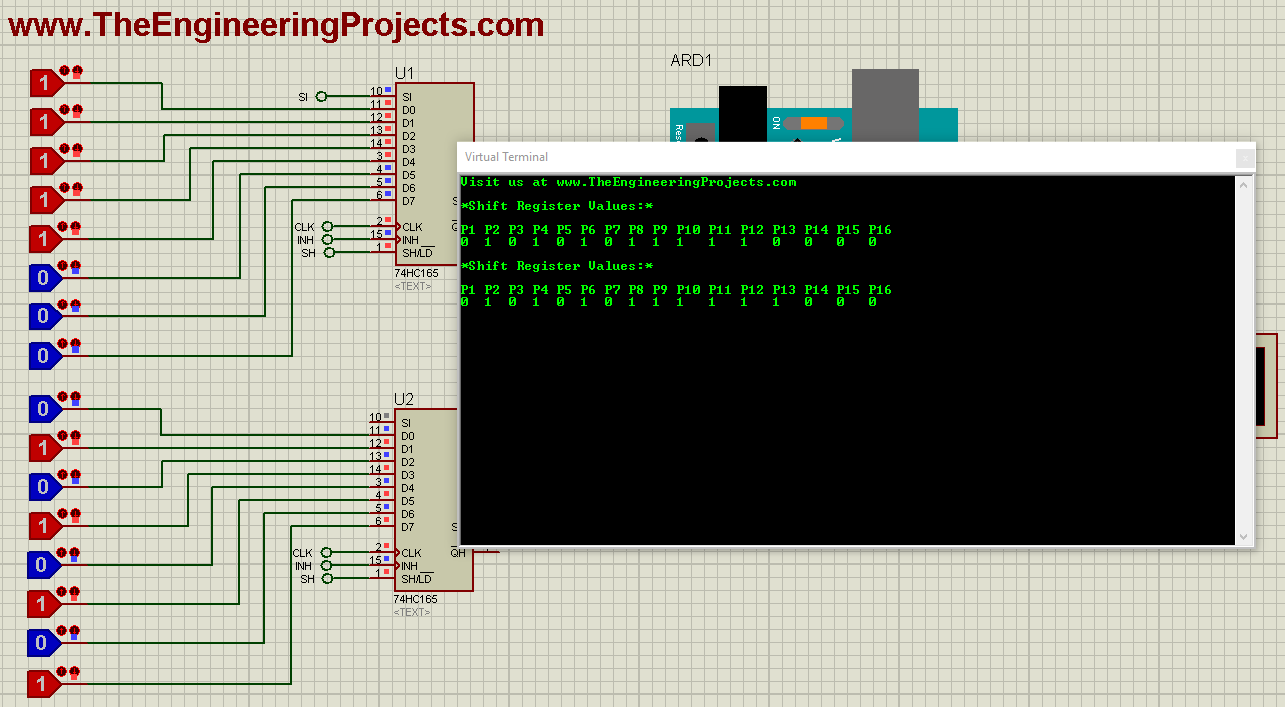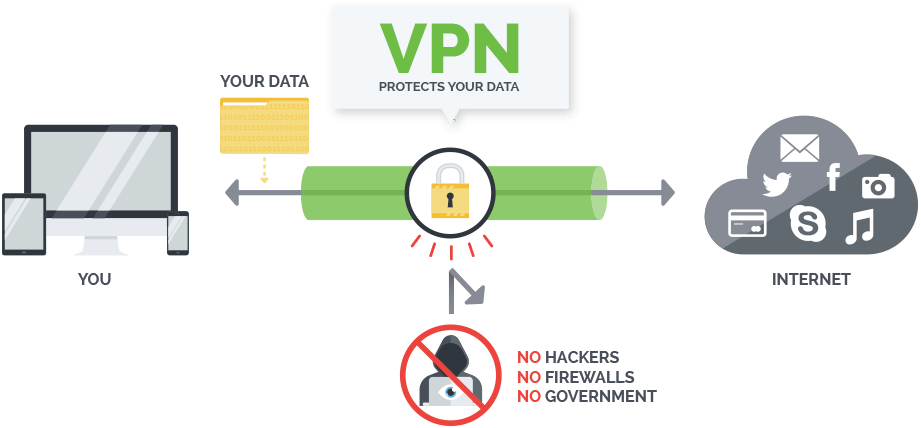

How Point-to-Point Tunneling Protocol (PPTP) Works



How Does PPTP Work?
PPTP incorporates factors of the even older Point-to-Point Protocol, or PPP. In this protocol, IP packets of data are encapsulated and transmitted to the VPN server. PPTP creates an encrypted tunnel between the VPN server and the customer's computer via TCP port 1723 as well as General Routing Encapsulation, also called GRE.- Essentially, this is a client-server setup that utilizes Layer 2 within the OSI model.
Image credit to Privacy Australia
How to Connect to PPTP
PPTP connectivity is a basic component that's integrated into popular operating systems such as Windows, MacOS and Linux. It's easy to set up and exceptionally easy to connect. The user launches their PPTP client, which will connect them to their Internet Service Provider. The PPTP then sets to work, creating a Transmission Control Protocol, or TCP, which manages the connection between the client and the server at the VPN. With the tunnel established, it is possible to transmit two categories of information. Control messages are used to manage and ultimately dismantle the VPN connection while data packets contain the information that passes through the tunnel.When Is It Appropriate to Use PPTP?
As an older VPN protocol, PPTP has several well-known vulnerabilities. If you're doing any sort of high-risk browsing or transmitting lots of sensitive data, then it may not be the best protocol. However, PPTP remains a popular choice for certain applications. Corporations still rely on this protocol to establish private tunnels through the publically available Internet. This essentially involves the creation of a wide area network that serves as a local area network that's larger than the usual LAN. The advantage of this approach is that the business does not have to lease private lines for wide-area communication. Nonetheless, they get the enhanced security that they need when employees are working remotely. With reduced transmission and hardware costs as well as lower administrative overhead, this can be an attractive solution for the right situation.×
![]()








 1 user
1 user






 Continue Wishlist
Continue Wishlist





 Getting Started Guide
Getting Started Guide
 Help Center
Help Center
 Contact us
Contact us
 Doist Blog
Doist Blog
 Privacy
Privacy
 Security
Security
 Terms of Service
Terms of Service
 What's new: Channel Descriptions
What's new: Channel Descriptions





 Tutorials
Tutorials syedzainnasir
syedzainnasir 0 Comments
0 Comments





 How Point-to-Point Tunneling Protocol (PPTP) Works
PPTP working
point to point tunneling
How Point-to-Point Tunneling Protocol (PPTP) Works
PPTP working
point to point tunneling

 Monday, December 3, 2018
Monday, December 3, 2018